Use IAP on Cloud Run without Load Balancers
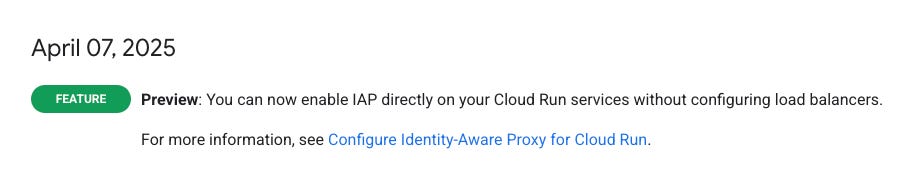
You can now enable IAP directly on your Cloud Run services without configuring load balancers (Preview)
It has just been announced (in public preview) you can now use Cloud Run with IAP (Identity Aware Proxy) directly without configuring Load Balancers.
Why?
This is quite exciting news! Why? For anyone who used App Engine before, you likely used App Engine with IAP without needing load balancers. That has been very convenient for hosting organisation-wide enterprise applications on a serverless platform on Google Cloud without needing much configuration.
Just to give a few examples from what I’ve seen of applications that can benefit from using IAP:
Internal Flask app for access management
Internal FastAPI app for data sharing
Internal GenAI app for call centre assistance
Internal app for monitoring application uptime
However, as App Engine has many limitations, including the lack of support for VPC Service Controls, using Cloud Run has become the recommended way forward for hosting these types of applications. Cloud Run is a very powerful service, often much more powerful and, in almost all scenarios, easier to use than App Engine. Unfortunately, this hasn't been the case for IAP-based applications.
The main reason is that it requires the use of a Load Balancer. I’ve discussed this over the past two years with Google SMEs, many industry experts, and other GDEs. The main reason for this design seems to be to provide better security. Technically, it is much more secure to have a clear separation between the front end and back end. Using a load balancer as the only way to access a backend service ensures there is no backdoor or duplicate implementation allowing direct access to the Cloud Run service, bypassing protections like Cloud Armor, etc. I’ve explained this in great detail in one of my YouTube videos. If you are interested in knowing more about this, feel free to check it out.
How does it work?
Now, the new release has made some changes here, allowing behaviour similar to App Engine on Cloud Run, meaning Cloud Run can now be configured with IAP without the load balancer.
This is great news in terms of convenience, but you might ask: does it contradict the security-by-design principle of separating the front end and backend?
I think the answer depends on several factors, especially the implementation details of how Google is safeguarding the service. Also, keep in mind this feature is still in public preview, so things may change.
From my point of view, several key considerations suggest this service can be well-safeguarded even without the load balancer.
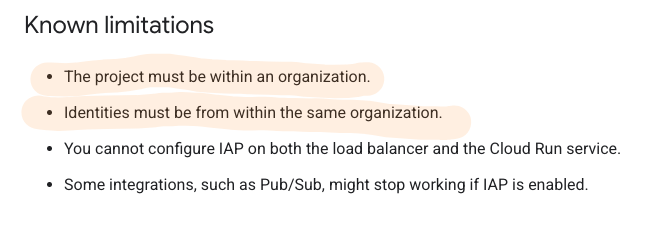
Regarding the known limitations section, I consider the first two points to be good safety measures. They help ensure you don’t accidentally expose the service to users outside of your organisation. This aligns well with the 'organisation-wide internal application' use cases, for which bypassing the load balancer setup seems particularly useful.
I’ve also tested this myself. If you try to grant access to a user (i.e., via their email address) outside of the organisation, it will not work with Cloud Run even if you give them the necessary IAM permissions, which is an excellent safeguard.
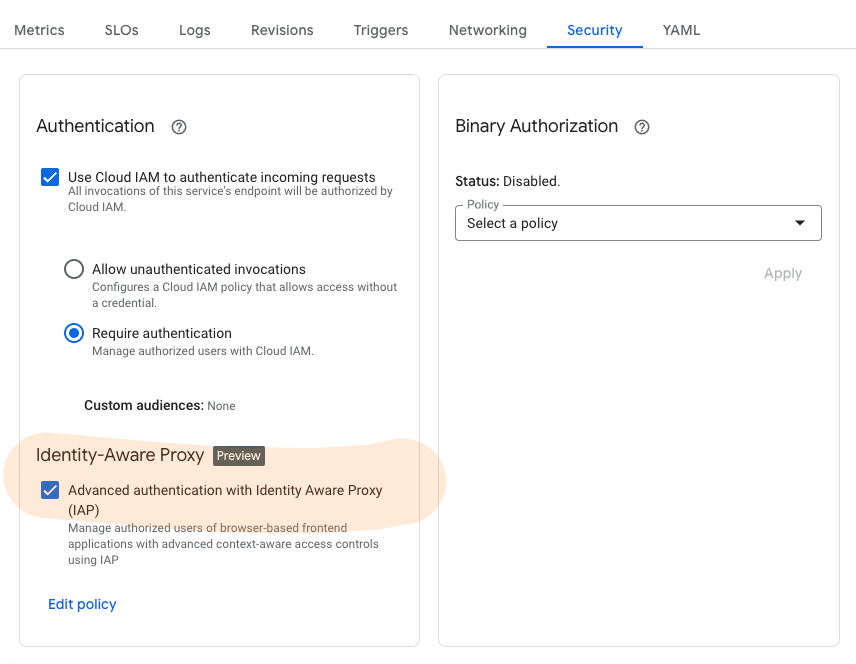
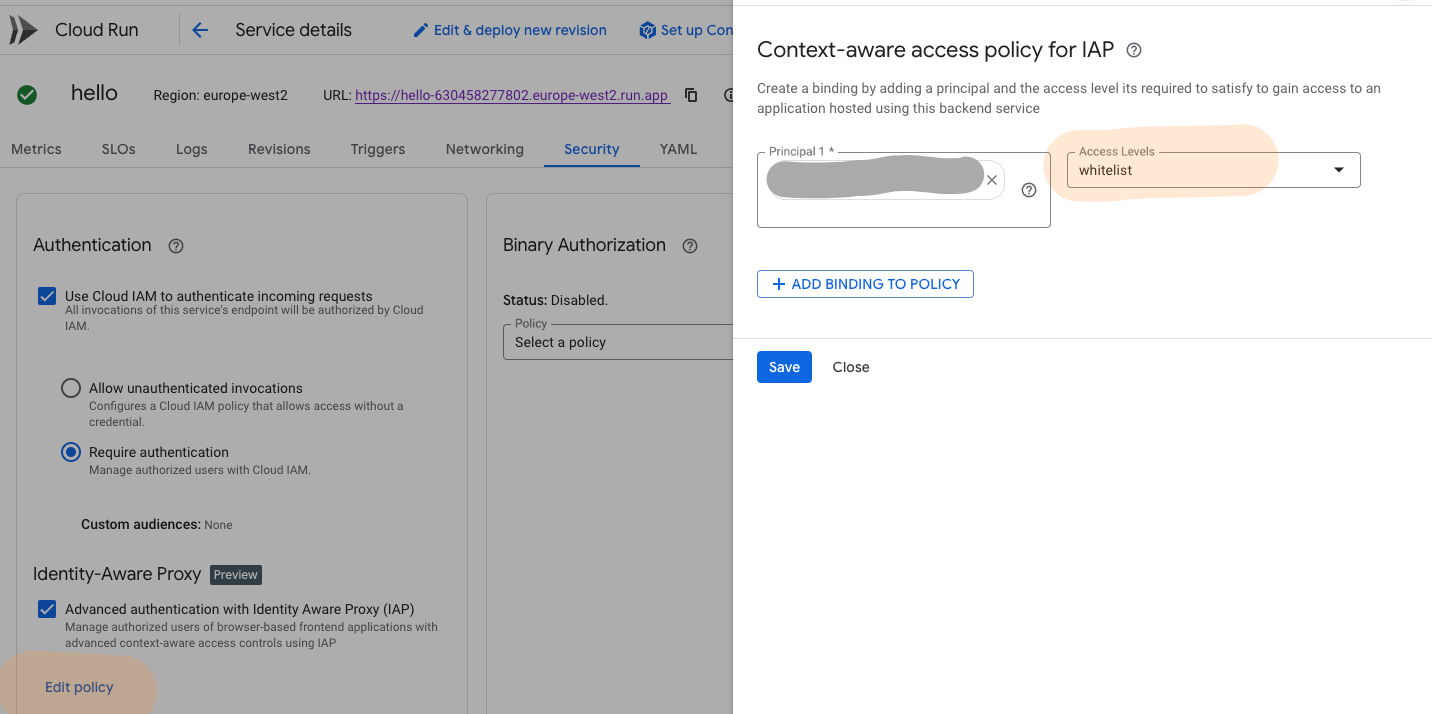
All you need to do is enable IAP under the Security section (or via the CLI / Terraform). You’ll then be presented with the usual SSO login page, prompting you to log in using either Google Workspace or your chosen SSO provider to authenticate to the application.
Potential issues
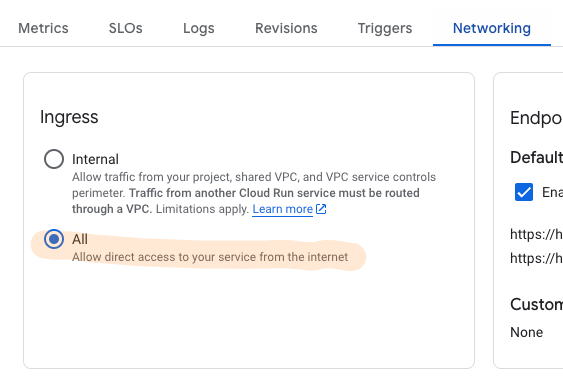
One thing however I couldn’t make it work as expected is the “Context-aware access policy for IAP”. This is an option you can consider using when enabling IAP for Cloud Run. It is useful because by default, you still have to open up the Cloud Run service to Internet Traffic.
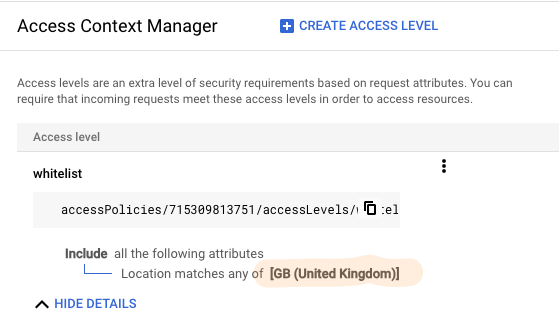
By adding policies such as a Whitelist of IPs or Regions to restrict only your desired IP space or IP addresses to gain access to Cloud Run provides another level of security. This is something you have to set when going through the Load Balancer, and is not something I want to lose as a feature.
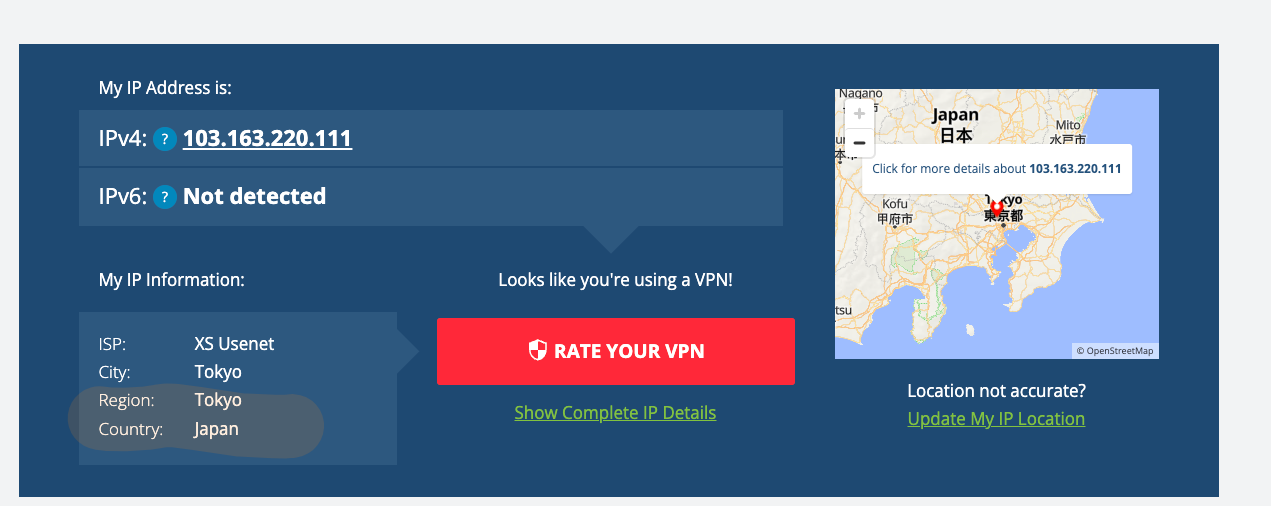
However, even if I enforce this, I can’t seem to get any errors and I can still access the Cloud Run service via IAP on a region that isn’t whitelisted.
Maybe I’ve overlooked some configuration but if anyone is able to enforce this please let me know, would be keen to know if something I did wrong here or it’s actually a bug.
VPC Service Control considerations
I couldn’t see much information regarding VPC Service Control (or VPC SC) support just yet. Typically, for a feature in preview, VPC SC isn’t supported. Therefore, I wouldn’t be surprised if you encounter some VPC SC-related errors when IAP is enabled for Cloud Run in this manner.
Having said that, VPC SC, when enforced, would be a great combination with this new IAP feature for Cloud Run (which allows bypassing the load balancer). This setup provides default protection even if the Cloud Run service is open to the public, literally giving you:
Level 1: VPC SC Network-Level protection
Level 2: Organisation-only user protection
Level 3: IAM permissions
So, even if you don’t configure additional Context-Aware Access policies, it is already a very secure setup out of the box.
Summary
Let me know if you find this useful, or if you have any insights on how you might like to utilise this new feature combining IAP with Cloud Run without Load Balancers.
From my point of view, this will make setting up internal, organisation-wide applications running on Cloud Run considerably easier, whilst remaining secure out of the box.